With the release of iOS 15, macOS 12 and the new iCloud+ service earlier this year, Apple introduced a new privacy feature called iCloud Private Relay. It is designed to help protect your privacy when browsing the web in Safari. But what does this new feature mean for your business? An overview.
How does it work?
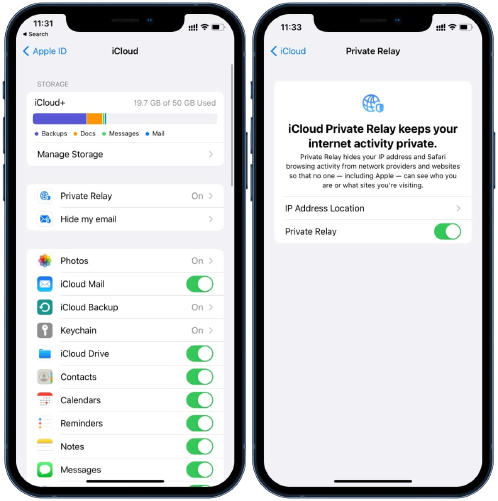
When surfing the web, essential information of you and your device, such as your IP address, DNS requests and the websites that you visit, can be collected, creating a profile of your location and behaviour on the web over time. By using two separate and secure internet relays, this information gets split, encrypted and anonymised resulting in no single party that can see both who you are and what sites you’re browsing when using Safari. The first relay is operated by Apple and will encrypt your DNS requests, so no one can see what website you’re visiting. The second relay is operated by a third-party service and will generate a temporary IP address, decrypt your DNS request and securely connects you to the desired website.
On your iPhone, you can turn on Private Relay in Settings > Click on your Apple ID > iCloud > Private Relay. In addition, you can finetune your IP Address Location. By enabling Maintain General Location your IP address stays hidden but websites are still allowed to show you localised content. When enabling Use Country and Time Zone a broader location will be used, but still within your country and time zone.
From an end-user point of view, this is excellent news. More privacy, less tracking, that sounds like an awesome package. But what if you’re in a strictly regulated business domain or what if you are running a web service that relies on that information? Let’s dive into some statements.
 A shadow IT nightmare?
A shadow IT nightmare?
Disallowing private relay on your network
If you have a network that requires to audit traffic or perform filtering, you may need to prepare your network to deal with Private Relay. The easiest way to do so is by preventing DNS resolution for the servers below. Do not drop IP packets or create a DNS timeout, because this will create delays on the end-user devices. Doing this results in the end-user being alerted on the device with the choice of turning of Private Relay for that specific network or to choose a completely different network. To disable it for a specific Wi-Fi network, take the device and go to Settings > Wi-Fi > tap the blue information button > disable Private Relay.
mask.icloud.com / mask-h2.icloud.com
Disabling access to private relay completely
This is where the MDM framework comes in. From the reference guide on the developers website we can see a new payload since a while. Make sure that your MDM solution supports this payload and if not, try to work with custom profiles to achieve the desired result. When clicking through to the network you’re connected with in your settings, you’ll see the option appear to enable or disable private relay.
Relying on the information of a web service
Offering localised content has been around since ages. Make sure that you are using the latest mappings from your geo IP database provider. Some providers annotate the addresses used by Private Relay, this helps when you need to dive into your connection log files. Remember that Private Relay preservers the country and time zone so offering localised content will be possible. Apple does provide a list with locations (https://mask-api.icloud.com/egress-ip-ranges.csv).
Great privacy on all Apple devices
No. Private Relay is not available (yet?) on Apple Watch. So using a weblink on your Apple Watch will expose your real IP address.
Private relay, a VPN service
No, it is not. First of all, it only works with Safari. And as mentioned earlier, it only hides your specific location and not your general region.
An equivalent for a mobile threat defense service
No, it is not. While Private Relay does anonymise web traffic, it will not prevent the user opening malicious websites or fraudulent text messages. If your organisation is looking for a MTD solution, come drink a coffee with us.
